What Your RF Signature Says About You
Presentation for BSides Perth 2018-09-15
Invisible, inaudible, and ignored, your devices are currently screaming out large amounts of information about you, your habits, your pattern of life to anyone who cares to listen. I will show you how to listen in, what is commonly being broadcasted, what can be done with this information, and how you can minimise the risks.
What Your RF Signature Says About You
This is me, Stephen. I was fascinated with how Sherlock Holmes could look at someone and see their life story. To counter this, I try and appear ordinary in public.
I could be anybody. No logos, no lanyards. But still, what I'm carrying is yelling out enough information that anyone who cares to listen can find my home, my work, see what electronics I own, and whether or not I've got a camera.
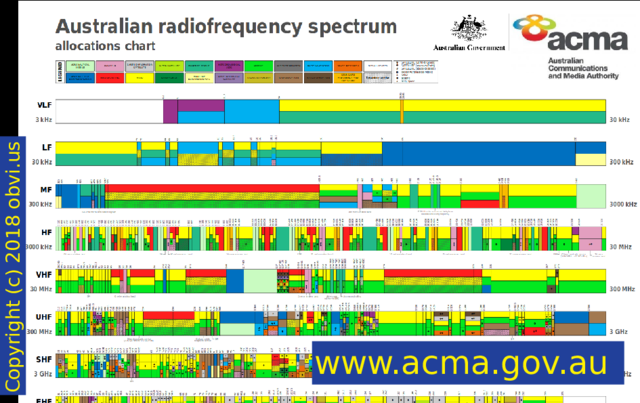
RF is "Radio Frequency". Every country publishes a chart like this showing the use of its frequencies. In the top left the frequencies are lower, the waves are longer, they travel for further, but they carry less data. Down in the bottom right they don't travel very far but can carry a lot of data. This is for Australia, from ACMA.
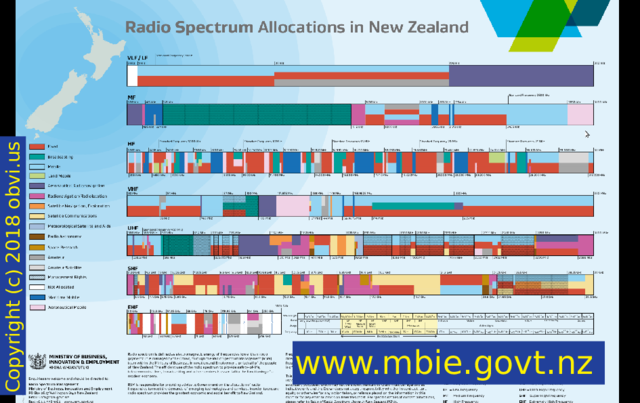
This is for New Zealand, from the MBIE.
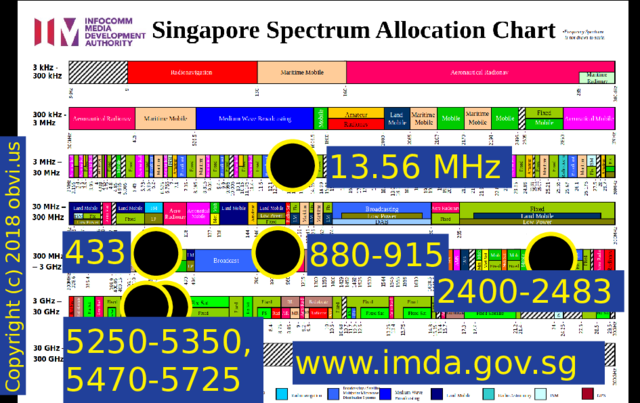
This is for Singapore, from the IMDA. I'm going to focus on the frequencies of 13.56 MHz, 433 MHz, 880-915 MHz, 2400-2483 MHz (2.4GHz), and 5250-5350 and 5470-5725 MHz (5GHz). These frequencies are interesting because you can broadcast on them unlicensed.
Two bands you're probably most familiar with are 2.4GHz and 5GHz for WiFi. WiFi networks are broadcasting on these frequencies to announce their presence. Routers are yelling out their name.
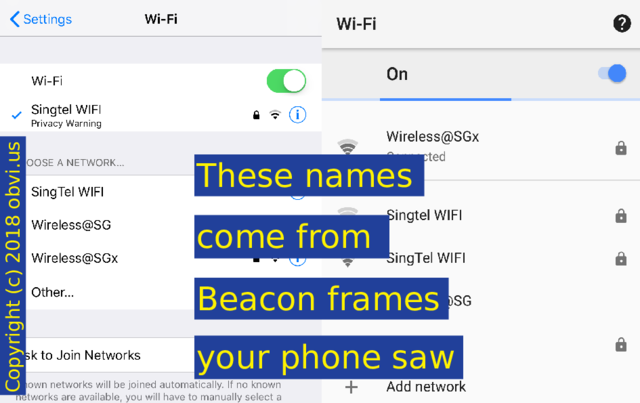
You're probably familiar with seeing a list of networks on your phone. All these names come from Beacon frames that your phone saw.
WiFi Beacon frames contain the SSID SSID: service set identifier -- the name -- of the network.
Useful tools: aircrack-ng and Wireshark
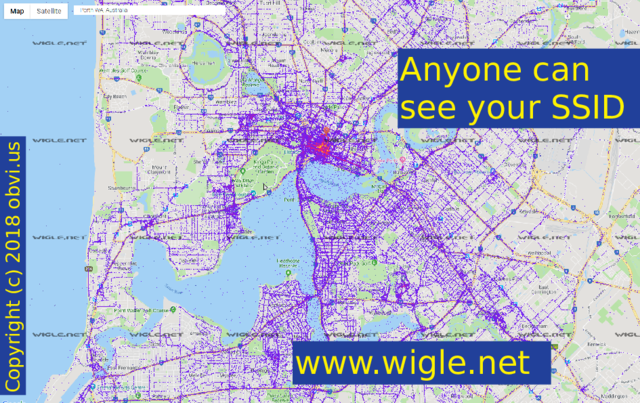
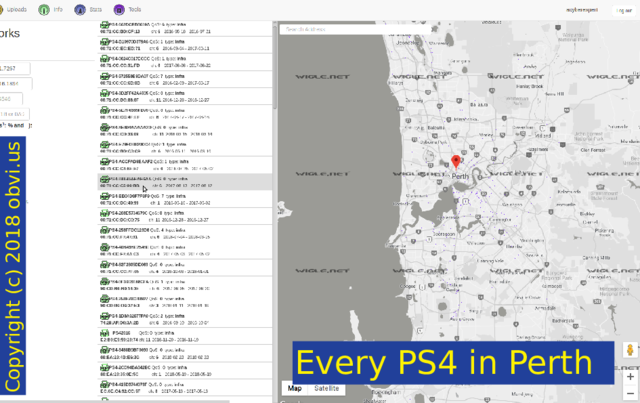
Anyone can see your SSID, and maybe put it on a map, such as this one of Perth. There are several services to do this. This one is Wigle. There is also Google, who violated the Skyhook patent.
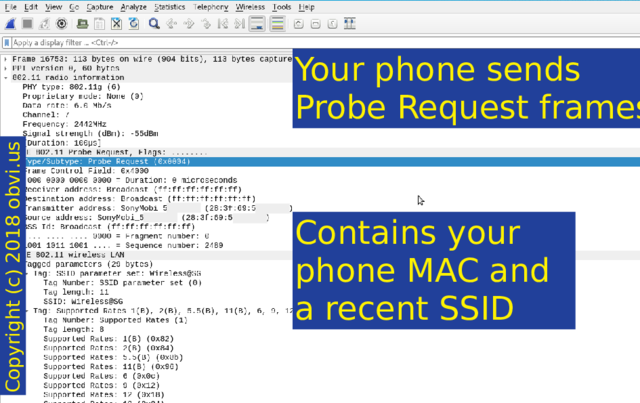
When not on WiFi your phone will yell out with Probe Requests, asking for a network to respond. The Probe Request contains your phone's MAC MAC: media access control address and a recent SSID.
I'll come back to this later. MAC addresses identify manufacturers. Each one is unique. And MAC addresses are not encrypted in WiFi frames.
Transport For London did a study TfL report (PDF) in 2016. They tracked Probe Requests from phones through the rail network. Already they had data on where people tapped in and out with their Oyster cards but they didn't know how people traversed the network and changed trains. Not every traveler runs Dijkstra's algorithm in their head. Afterwards TFL improved signage to help travelers change trains more efficiently. So this is a benevolent use of phone tracking and it works because your phone sends out Probe requests.
Introducing the Cyber Kill Cyber Privacy Cyber Chain! It's Pat Pending. How it works is you 1. sniff an identifier, eg, a SSID. 2. Then you sniff another identifier, eg, a MAC. Sniff another and repeat as required. 3. Build pattern of life. 4. Dot dot dot. I'm waiting on Patrick for this step. 5. Then money and early retirement.
Is anyone reading this currently in Starbucks? Probably not. But your phone doesn't know and it will happily join Starbucks Free WiFi
.
Suggestion: Turn off your WiFi if you don't expect to be using it.
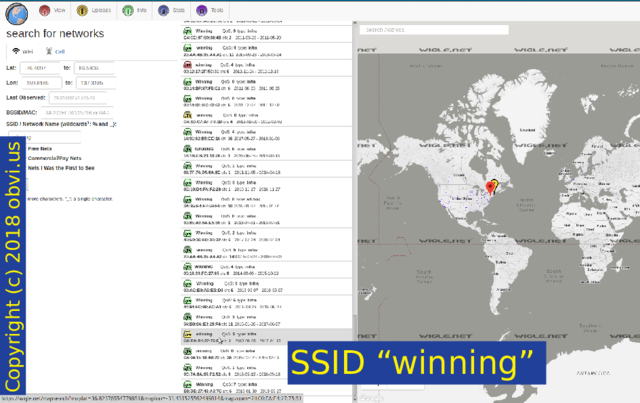
Newer Androids will randomise the MAC that it sends, but the SSIDs are not randomised. I stuck out an aerial to get an example of a list of SSIDs sent out by a single phone and received this. You'd think I'm making it up. It tells the story of this person's holiday: they're at a hotel in Singapore, go to Changi Airport, take a flight to China - business class, go to Starbucks there, visit an Apple store, at another hotel, another flight, now they're using Fios, and finally ... winning.
I thought maybe "winning" was unique enough to locate their house but fortunately for them it is a popular name. They could be anywhere in North America. Good for them.
Suggestion: choose a boring WiFi name (not your own full name)
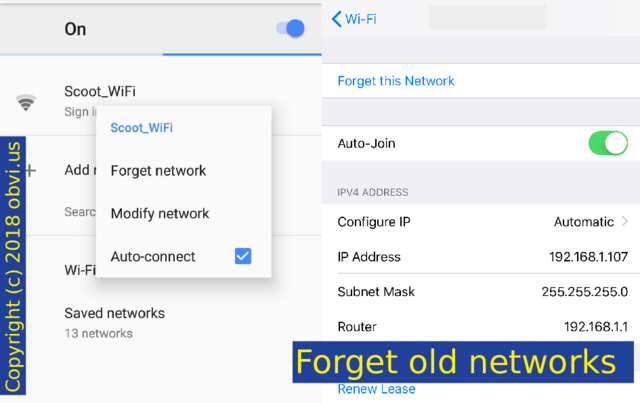
Once again, forget old networks. Android has a list of Saved networks. iPhone is a bit more difficult: you have to currently be on the network to forget it (or just reset all your network settings).
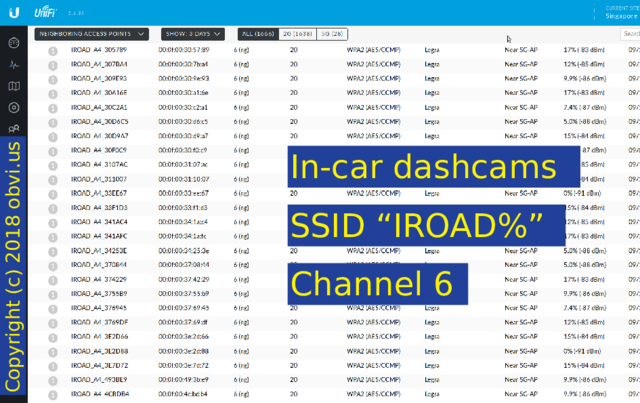
Other devices broadcast a unique name: for example, IROAD dashcams. Here is a list of people with this dashcam that drove past my house yesterday. I didn't ask: they told me!
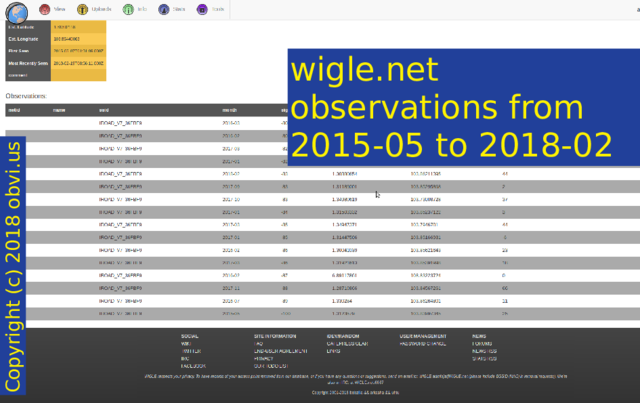
And here are a bunch of places that one car has been seen over the last 3 years.
Other dashcams do this too.
Reminder: MAC addresses identify manufacturers MACs are in blocks called OUIs (Organizationally Unique Identifier) which are dished out to manufacturers. The first half of a MAC address is the organisation and by extension the device it is in, the second is your specific device. . Each one is unique. And MAC addresses are not encrypted in WiFi frames.
Because of this we can see a list of all the devices on the network. You can see an Apple phone, a Sony Xperia phone, and a Raspberry Pi. Even further, you can see the wired devices too. Eh?
Useful tool: Kismet Wireless
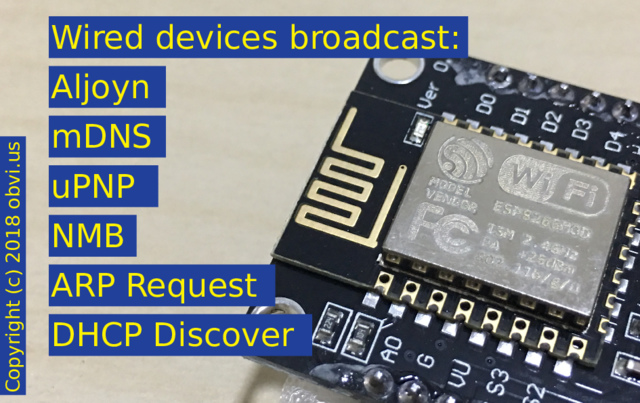
Wired devices broadcast. They all want to yell out that they exist. Many protocols broadcast their presence on the wired network and that broadcast gets dutifully transmitted over WiFi: Alljoyn, DLNA, mDNS, uPNP, Dropbox, Spotify, Chromecast, outdated NMB (Netbios), and of course underpinning protocols such as ARP Requests and DHCP Discover.
Pictured: ESP8266MOD (same as conference badge)
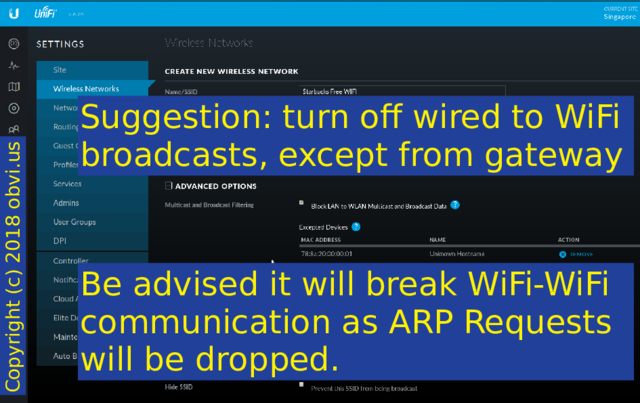
Suggestion: turn off wired to WiFi broadcasts, except from your gateway (both the internal and external interfaces - UniFi only populates one).
Be advised that this will break WiFi to WiFi communication as ARP Requests will be dropped. This took me two weeks to figure out. I just saved you five hours. You're welcome!
Here's every PS4 in Perth. This isn't every PS4 in Perth as not everyone will have been mapped out on Wigle. Also, PS4s have dual interfaces, a "Sony Interactive Entertainment" wired interface and a "Hon Hai Precision" Wi-Fi interface. I searched by SSID and not by either MAC OUI.
If your surveillance camera is not wired then someone can sniff the traffic - even encrypted - and do traffic analysis.
Some ASCII art showing a flat line. If there is hardly any traffic, then the network is idle. There is no camera active here.
If there are sudden spikes of traffic but otherwise idle, the surveillance camera is using motion detection. When it detects motion it broadcasts the traffic, sends someone an alert.
Well lit pictures with more detail in them are harder to compress than dark pictures at night. If the amount of traffic slowly increases around sunrise and decreases at sunset then the camera is streaming video the entire time but it doesn't have active infrared for night time.
What does this graph show?
I went to the toilet at 2am and turned on a light.
Suggestion: Wire your camera.
Whilst finishing my slides I stumbled across this paper which does traffic analysis of devices and explains the methodology in more detail: Peek-a-Boo: I see your smart home activities, even encrypted. There was also another paper in 2018 which involved drones and that got much more media attention because it involved drones.
880 - 915 MHz is interesting because it's the lowest GSM uplink band within reach of cheap SDR tuners. If they're not sending their video via WiFi then maybe they're sending it over the cell phone network.
Speakers, soundbars, headphones, mice, phones, earpieces, all communicate with Bluetooth. Again, they have a unique MAC. Try a Nordic nRF52840 Dongle.
Also rental bikes. If they have a FCC certificate ID stamped on them it's a good indication they can broadcast.
Bike lights.
Suggestion: don't pair in public
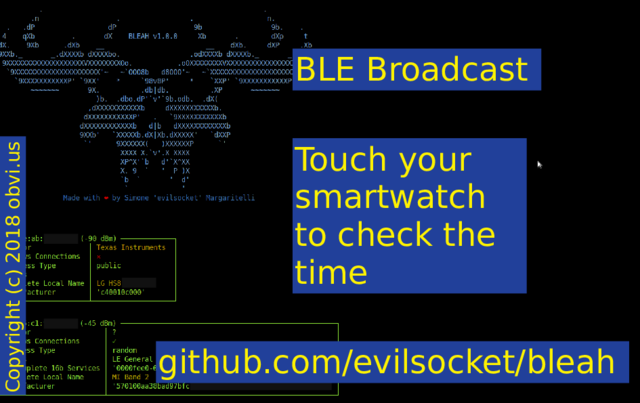
Bluetooth LE (Low Energy) is also on 2.4GHz but it sends beacons less often. It is used for fitness trackers, scales, smart watches, and GoPro cameras.
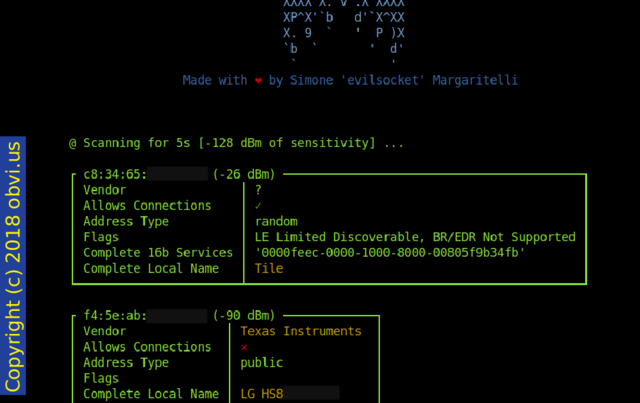
Bluetooth LE (BLE) devices also have a unique MAC. You can see the manufacturer and often the device name. Touch your smart watch to check the time and it will broadcast its presence. I'm using bleah to see this. When trying to get this example my neighbour's sound bar decided to jump in.
Tiles use BLE to help you find your keys or wallet.
Fun fact: You cannot be tracked by Tiles. It says so in the license agreement: You agree not to ... intercept or sniff the communication packets
. Secure!
Skipping to the next slide...
ANT+ is a protocol from Garmin for their sports equipment. I have not examined this protocol closely.
Zigbee, also on 2.4GHz. Get a CC2530 or similar chip to sniff it.
Another fun frequency: 433MHz. You will find cars broadcasting on this. The Tire Pressure Management System will yell out the temperature, pressure, and also a unique serial number. 433 MHz will also travel further than WiFi. You can get a really cheap SDR (about $11) based on the RTL2832U chip and then install rtl_433 to decode the broadcasts.
Also on 433MHz: your dinner.
13.56 MHz is where NFC lives. Visa PayWave and MasterCard PayPass put aerials into credit cards, wire them into the chip. They don't actively broadcast but a card reader must be brought near them to energise them. Dangers about stealing money are overblown. Tapping the card isn't the end of the story: there is a merchant bank, credit card processor, card issuer, card holder's bank, and my credit card statement. Thieves won't get away with money, but they can get away with ...
... your full name! Track data that can be read over NFC includes the card number (excluding CVV), expiry, and your name on the card.
You can mitigate this with a Blocking Card (commercial plug for my cousin here, he gave me this card after we were playing with NFC card readers) or make life difficult with a metal wallet.
Cyber Kill Cyber Privacy Cyber Chain:
- Sniff an identifier,
- Sniff another,
- Build pattern of life,
- ... (hurry up Patrick!),
- Applause and break for lunch.
Thank you, you've been a great audience.
Question time: what brand is my NAS?
All Privacy Suggestions
- Turn off phone WiFi when out
- Forget old networks
- Use a boring WiFi SSID (not your name)
- Disable Wired to WiFi broadcasts
- Migrate to 5GHz-only if possible
- Wire your cameras
- Pair Bluetooth devices at home
- Put your cards in your wallet
- Keep work logos and ID cards hidden
Like what you see? Follow @acyberexpert on Twitter, or Contact me for more, including any clarifications on this article, further speaking engagements, offers of radios or radio equipment, or anything at all.