Replacing OpenSSL with LibreSSL
This page was last updated in 2016-04-01. General information is approximately correct, but it may have improved since then. (eg, last I looked there was no TLSv1.3 support in LibreSSL.)
LibreSSL is a fork of OpenSSL which is maintained by the same people that brought us OpenBSD and OpenSSH. It provides a pretty good drop in replacement for OpenSSL.
Building from source
Due to the pace of updates for LibreSSL and OpenSSL you may enjoy building your own packages, rather than waiting for upstream maintainers to put them together for you. The build for LibreSSL is a fairly close drop in for OpenSSL, but here's a guide just in case.
Make sure your have all the pre-requisite pieces to build it. Look in the Additional packages section for those.
Make sure you have git as we'll be pulling this from github.com, rather than using a tarball.
Getting LibreSSL
Normally I fetch and extract the source for OpenSSL like this:
$ wget https://www.openssl.org/source/openssl-1.0.2g.tar.gz $ tar zxf openssl-1.0.2g.tar.gz
LibreSSL also lives on github. It doesn't offer the same tarball download, however, and uses git as part of its build.
Now, get and clone LibreSSL portable from github:
This fetches LibreSSL portable after which you run autogen.sh which pulls in the LibreSSL source and does all the autoconf and libtool magic, and then you go and build it:
$ git clone https://github.com/libressl-portable/portable.git $ cd portable $ ./autogen.sh
This will check your build setup, fetch LibreSSL, run through autoconf/automake/libtool and patch it for your setup.
Now you've got the source you're ready to build it.
openssl standalone
The command line utility openssl that we use as a general purpose crypto tool is available in libressl. It's still called 'openssl' (just change your PATH to point to the libressl on instead of your system default one) and has the same commands, but it has modifications to its underlying code and some new cipher suites, which I detail below.
$ ./configure --prefix=/opt/libressl --enable-nc $ make check $ make install
This contrasts a little to the OpenSSL build for the same thing, which would look like:
$ ./configure --prefix=/opt/openssl $ make shared $ make install
nginx
Normally I build nginx like this:
$ cd /build/src/nginx $ ./configure ... --with-http_ssl_module --with-ipv6 ... --with-openssl=/build/src/openssl-1.0.2g
So just drop in 'portable' where you normally have OpenSSL. Couldn't be simpler.
$ cd /build/src/nginx $ ./configure ... --with-http_ssl_module --with-ipv6 ... --with-openssl=/build/src/portable
You do not automatically take advantage of the new ciphers. You have to configure for those. A simple way is to add them to the front of your ssl_ciphers line:
ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-CHACHA20-POLY1305:...';
While you're there you can also check your dhparam, your Strict-Transport-Security and your Public-Key-Pins settings (in this case for Let's Encrypt Authority X1 with no backup pin). If you're copy+pasting them from this page I've set the time limits to be quite low.
ssl_dhparam /etc/nginx/dhparam.pem; add_header Strict-Transport-Security "max-age=86400"; add_header Public-Key-Pins 'pin-sha256="YLh1dUR9y6Kja30RrAn7JKnbQG/uEtLMkBgFF2Fuihg="; pin-sha256="Vjs8r4z+80wjNcr1YKepWQboSIRi63WsWXhIMN+eWys="; max-age=86400';
Additional packages
As the files in libressl-portable haven't already had autoconf and libtool run over them then in addition to your normal build packages you'll also need to install those (sudo yum install / sudo apt-get install):
autoconf automake libtool m4 patch
This is in the README.md
Differences between LibreSSL and OpenSSL
Aside from the deep down changes (improvements to the API, tidying of the code, catching a few errors) there are more obvious ones too: CHACHA20!
Run 'openssl ciphers' and you'll see some new ones that OpenSSL doesn't offer:
$ /opt/libressl/bin/openssl ciphers | tr : '\n' | grep '\(GOST\|CAMELLIA\|CHACHA20\)' | sort CAMELLIA128-SHA CAMELLIA128-SHA256 CAMELLIA256-SHA CAMELLIA256-SHA256 DHE-DSS-CAMELLIA128-SHA DHE-DSS-CAMELLIA128-SHA256 DHE-DSS-CAMELLIA256-SHA DHE-DSS-CAMELLIA256-SHA256 DHE-RSA-CAMELLIA128-SHA DHE-RSA-CAMELLIA128-SHA256 DHE-RSA-CAMELLIA256-SHA DHE-RSA-CAMELLIA256-SHA256 DHE-RSA-CHACHA20-POLY1305 ECDHE-ECDSA-CHACHA20-POLY1305 ECDHE-RSA-CHACHA20-POLY1305 GOST2001-GOST89-GOST89 GOST2012256-GOST89-GOST89
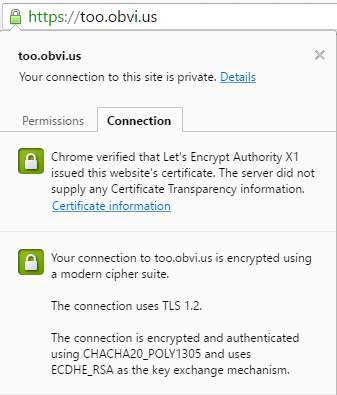
So there are new cipher suites that you're able to use when making connections out, using the standalone 'openssl' utility, or accepting connections in with nginx or something built with LibreSSL.
You can see this when connecting out:
$ /opt/libressl/bin/openssl s_client -connect too.obvi.us:443
...
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-CHACHA20-POLY1305
Compare this with OpenSSL 1.0.2g:
$ /opt/openssl/bin/openssl s_client -connect too.obvi.us:443
...
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES128-GCM-SHA256
You'll make Chrome happy ... but not much else so far!